With the complexity of today’s IT infrastructure and the applications running on networks there is always a risk that something goes wrong. Consequences can be a significant loss of revenue because of production stops, potential safety or health problems if inaccurate data transfer led to inaccurate reporting of laboratory results with consequent inadequate releases of batches and problems during FDA inspections if data are lost through a server error.
Situations like this can be avoided to a large extent or their damage can be reduced at reasonable costs by applying modern risk management strategies. Possible hazards and subsequent harms are identified, their probability of occurrence and severity estimated, and actions are then taken to mitigate the risks.
Typical problems with network infrastructure are:
- Hard drive failure on the server can cause severe system downtime and loss of data.
- Loss of network connectivity due to hardware failure, e.g., network interface card, can cause system downtime.
- Network overload can cause slow-down of network operations and system downtime.
- No specifications on vendor support in the purchasing agreement. This can result in reduced uptime because of missing support in the case of hardware, firmware or software problems.
- No documentation of installation can make it difficult to diagnose a problem
- No drawings can make it difficult to diagnose a problem
- No verification of the accuracy of a file transfer can cause inaccuracy of results
- No verification of security access functions can result in access to the network through unauthorized people.
- No plan for system back-up. This can result in decreased uptime in the case of a system failure and in loss of data.
- No plan for rollback if updates don’t work as expected. This may cause severe system downtime through reinstallation and re-configuration.
- No documentation of hardware and software changes makes it difficult to diagnose a problem.
High Level Evaluation and Assessment:
For high-level risk assessment of network infrastructure we follow the steps as outlined in the article : “How to create Risk Management Master Plan For FDA Regulated Companies“
Networks are categorized as high, medium or low risk. The result of this exercise is used to decide if and to what extent Part 11 requirements will be implemented or if it is worth developing and implementing a detailed risk management plan for a specific process or system. Proposals for such assessments are made by IT staff and approved by the risk management team.
The resulting risk level information is used for considerations such as:
- How extensively do we test the network components and communication? For example, high risk systems will be tested under normal and high load conditions.
- How much back-up do we need? For high-risk infrastructure we should have qualified back-ups for all hardware components.
- For medium risk networks a back-up of the most critical components is enough and for low risk systems there is no need for hardware back- ups.
- How frequently do we have to back-up data stored on the network database?
Factors contributing to high risk networks are:
- Used in regulated applications
- Used in manufacturing environments
- Used in production quality control environments
- Product quality problems may permanently impact people’s health.
- Network components hold confidential data
- Probability of detecting and correcting errors is low or zero.
- Must run 24 hours a day, 7 days a week.
- Highly complex
- Highly customized hardware and software
- New technology
- No support from vendor, e.g., no documented evidence on testing network devices, or no phone or on-site support in case of problems.
Factors contributing to low-risk systems are:
- Not used in regulated applications.
- Used in early product development stage.
- Product quality problems may not have any impact on people’s health.
- Probability of detecting and correcting errors is high.
- No customization of hardware and software
- Technology bullet proof.
- Downtime not critical
- Support from vendor, e.g., documented evidence on testing and local language phone support and/or on-site support in case of problems.
The basic questions to be answered for this assessment are:
- What is the impact of the network on a company’s business and on product quality and how big is the problem if data stored or transferred are lost?
- What is the likelihood that the network fails?
Sample Checklists help to identify risks and activities to control the risk is given below.

Detailed Risk Management:
For a detailed evaluation and control of individual risk factors we follow the steps described in the article “How to create Risk Management Master Plan For FDA Regulated Companies“
Detailed risk management should cover all lifecycle phases. Risk factors should be identified for:
- Setting specifications
- Purchasing
- Pre-installation
- Installation
- Testing
- On-going use
- Changes
- Retirement
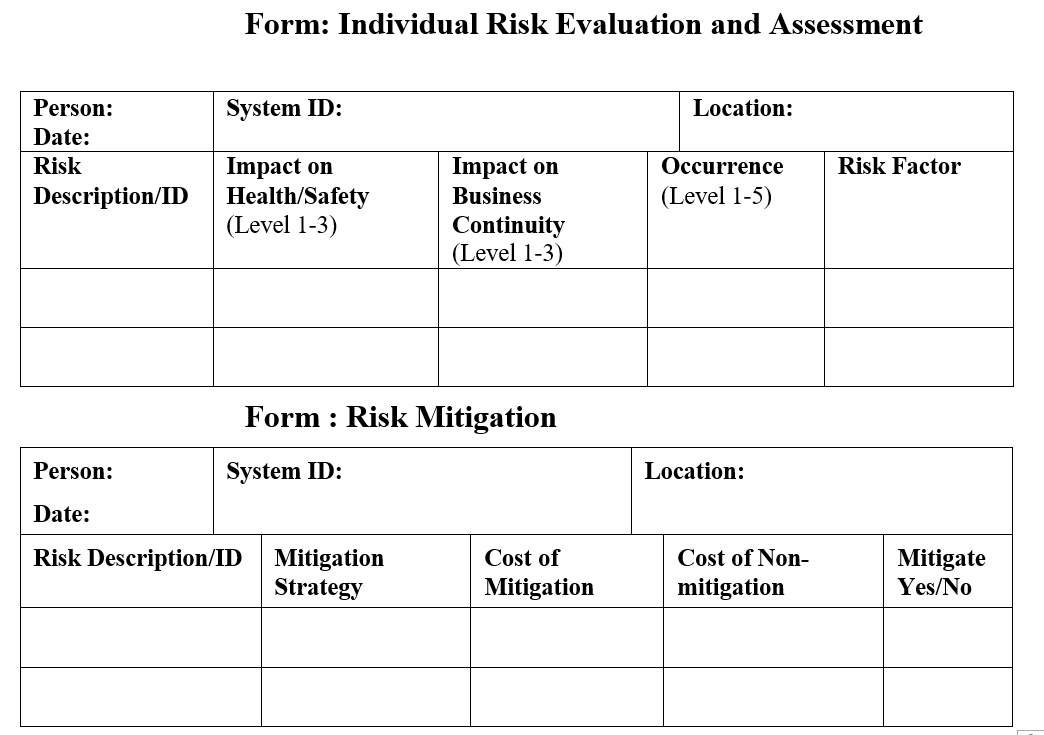
Below forms can be used for documenting mitigation and observations during on-going use
Related Articles :
How to do Risk Management of Computer Systems Used for FDA Compliance
How to do risk assessment of Spreadsheet and Macros
Risk management of existing(Legacy) systems for FDA Compliance
